by Jennifer Daffron and Kelly Quantrill

The nearly 24-hour outage of the O2 4G network that affected O2’s 25 million customers has been traced to an expired certificate in a software used by their supplier Ericsson.
What exactly does this mean? What kind of certificate has the power to impact individuals in over 11 countries including the UK and Japan? Likely, it was a TLS Certificate.
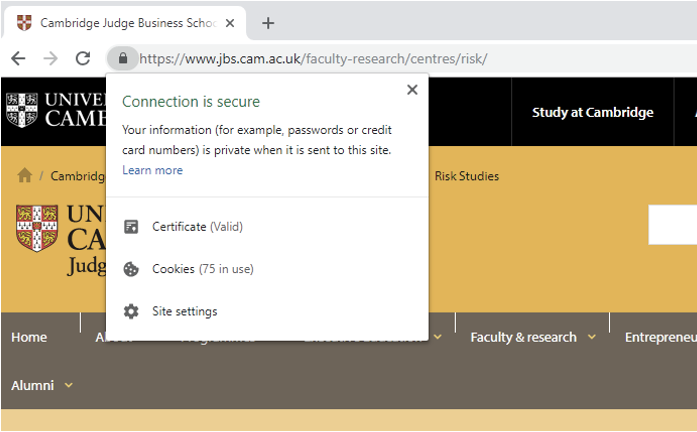
TLS provides a secure channel between two machines or devices operating over the internet or an internal network. It is the most commonly used protocol for web security. The certificate authenticates the identity of the devices to ensure your web traffic is secure, ensuring you are communicating with the end user you think you are and not an illegitimate website. This is confirmed with the ‘lock’ box seen in web-browser address bars, as highlighted below.
TLS Secure Communications are used in almost all secure traffic on the internet including communication in web-browsers, websites, email security, and cloud services.
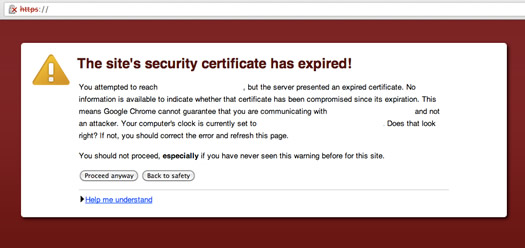
When the connection is no longer valid, devices can warn you about the security of the website, as in the image below, or prevent you from communicating with it entirely, known as a ‘hard fail’. In some cases, the devices communicating with each other do not have a public facing interface and thus will force the shutdown of a device when it is no longer secure.
While certificate expirations are typically monitored closely, this is not the first time such an event has had a global impact. In 2013, Microsoft’s Azure cloud storage experienced a worldwide outage impacting HTTPS operations (TLS traffic) due to an expired certificate causing performance problems in up to 52 different Microsoft services during the outage, including Xbox Live. This outage lasted 12 hours for most users but as many as 24 for others. Both this event and yesterday’s O2 outage could easily have been avoided.
The loss of 4G and 3G networks in some areas impacted many jobs which require constant access to the internet including Transport of London and a number of NHS trusts. The CRS Cyber team will continue to monitor the outcomes of this outage as more information becomes available to determine the loss impact of this event. The team has also been working on a disaster scenario on this topic which will be released in 2019.



Leave a Reply